Why Secure Workspaces Are Critical

Introduction: The Security Crisis Facing Modern Teams
Gartner’s top cybersecurity trend for 2025 isn’t about firewalls or encoding—it’s about protecting unstructured data: the texts, images, and videos now fueling GenAI models and business workflows alike. The crown jewels aren’t just rows in a database anymore; they’re sitting in chat threads, screenshots, and video calls.
This shift happened gradually. What started as casual chat apps evolved into business infrastructure. Now, with Mimecast reporting a 7% uptick in attacks on tools like Slack and Teams, and 79% of security leaders warning that these apps introduce fresh vulnerabilities, securing your collaboration workspace isn't optional—it's survival.
Thirty years ago, a hacker might have been dumpster-diving outside an office at 2 a.m., sifting for tossed-out documents with machine names or even passwords. Today, AI does the dumpster-diving—at a global scale, carpet-bombing style, scanning code repos, misconfigured buckets, and public forums. And instead of one intruder trying door handles, it's a horde of intelligent bots that learn from each failed attempt until something breaks. Every decision about where and how your team collaborates has become a security decision.
I’ve spent the past decade alongside CTOs, CISOs, and IT leads watching security evolve from “a compliance checklist” into the business’s survival strategy.
Why should I reconsider my workspace security in 2026?
Because the threat landscape has shifted from possible to persistent. Verizon’s 2025 Data Breach Investigations Report logged 22,052 incidents, with 12,195 confirmed breaches—the highest count in the report’s 18-year history. Worse, sensitive information exposed in public GitHub repos sat unremediated for a median of 94 days, plenty of time for attackers to scoop it up. Staff shortages in cybersecurity make things even harder, affecting 26% more companies than year before.
Meanwhile, AI-powered attacks are no longer exotic—they’re becoming the default playbook. Adversaries now use machine learning to analyze communication patterns, craft phishing messages indistinguishable from colleagues, and time them for maximum impact. Gartner puts it bluntly: cybersecurity isn’t about blocking every shot anymore—it’s about making sure the business keeps running when the punches inevitably land.
And leadership is worried. According to IBM’s Institute for Business Value, 51% of business leaders are concerned about unpredictable risks and new vulnerabilities, while nearly half specifically fear AI-driven attacks.
The new mandate: build resilience into human behavior within a secure collaborative environment, use dynamic nudges to shape safer habits, and clamp down on third-party risk before it metastasizes.
Who are the intruders and what motives are driving them?
According to Verizon’s 2025 DBIR, external actors dominate the breach landscape. Take the Information sector: 83% of breaches came from outside attackers, not rogue insiders or careless partners. Their motives split along two telling categories: 78% were financially driven, from classic ransomware schemes to outright data theft for resale, while a striking 36% were tied to espionage. That mix shows today’s adversaries aren’t just cybercriminals chasing quick payouts—they also include industry spies and state-linked groups probing for long-term advantage.
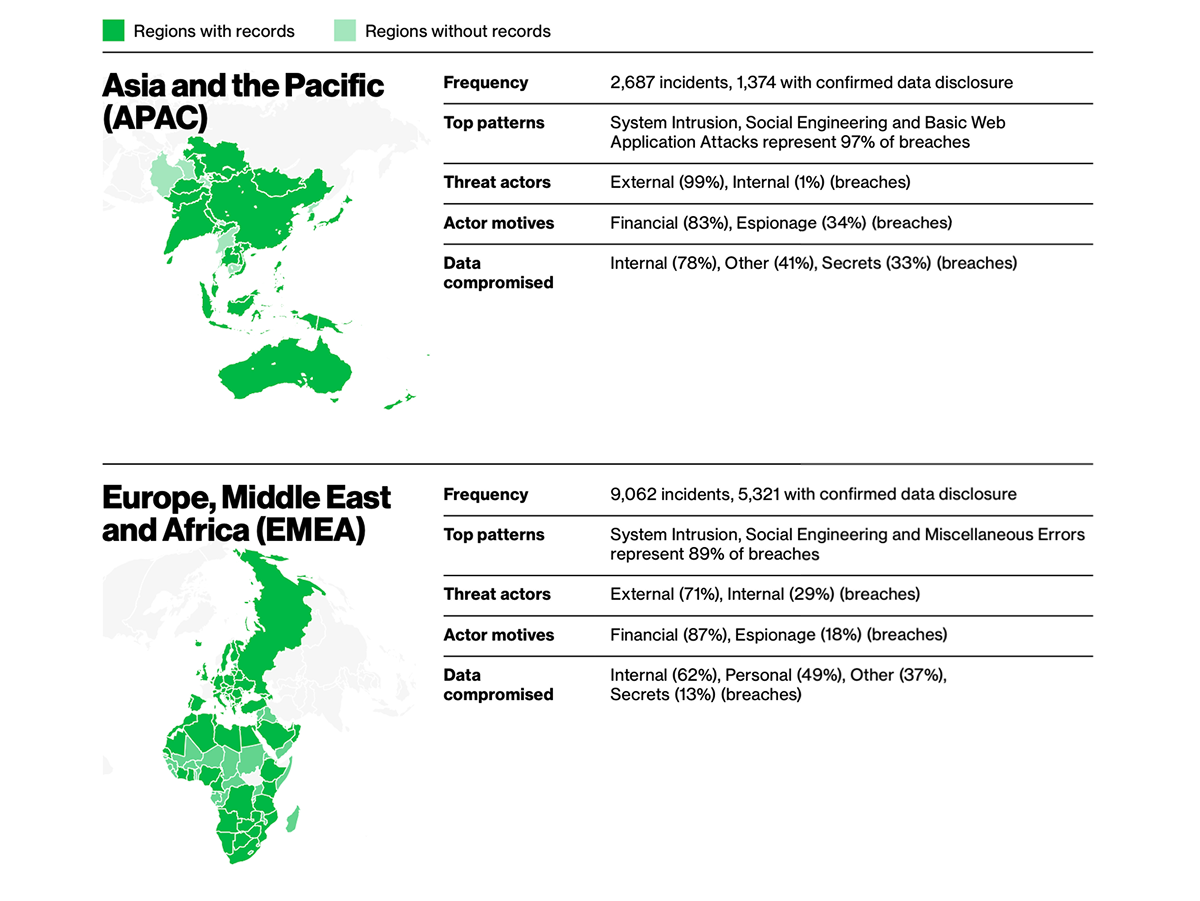
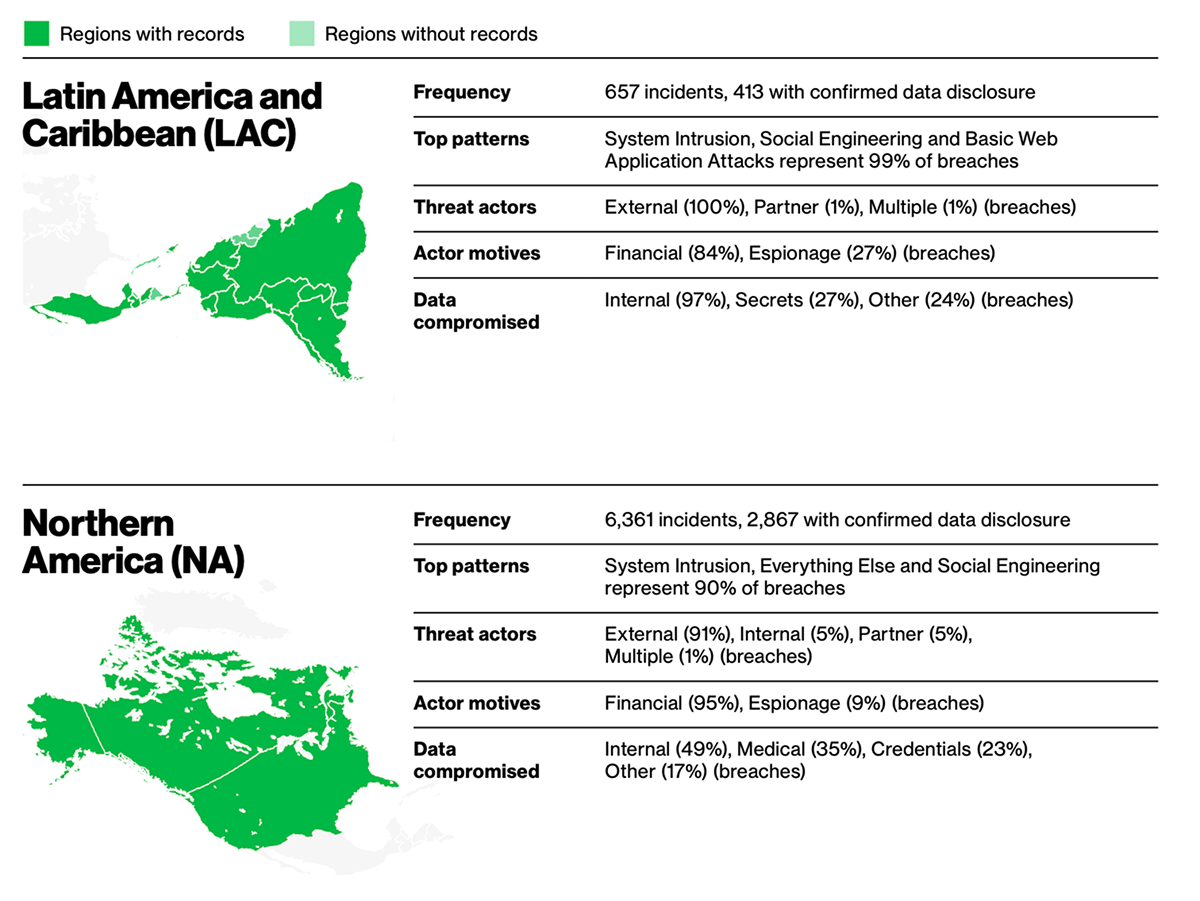
What are the biggest security threats to team collaboration and messaging?
At the end of the day, it’s still ignorance. Verizon’s DBIR shows the human element drives about 60% of breaches. And when the weakest link is the way people actually use their tools, collaboration apps become the front door for attackers.
Here are seven threats that put your employees directly in the crosshairs:
- AI-Driven Phishing – Hyper-personalized lures that used to take a week to craft are now generated in seconds by generative AI. The result: more believable scams at internet scale.
- Session Hijacking – When authentication tokens are stored insecurely, attackers can impersonate legitimate users. Researchers have shown how Microsoft Teams stored tokens in plain text, making them easy to steal and reuse (BleepingComputer). In another well-known case, Slack employee tokens were stolen and used to grab Salesforce’s private GitHub repositories (Slack Security Update).
- Shadow IT Messaging – Employees using unmanaged devices (BYOD) or unauthorized apps for work chat. A single login reused on a personal phone can widen the attack surface dramatically.
- Persistent Chat Histories – Sensitive information living forever in searchable chat logs. That is convenient—but it also means sensitive credentials can resurface long after they should have been wiped.
- Software Supply Chain Vulnerabilities – Every third-party integration adds risk. Already mentioned Verizon's Investigation highlights how third-party involvement has doubled in just one year, from 15% to 30%, underscoring the danger of inherited exposure from your app ecosystem.
- Data Residency Violations – Governments aren’t just regulators; sometimes they’re interested parties. Mislocated data can mean multi-million-dollar fines—or worse, legal backdoors to your information.
Metadata Leakage – Even encrypted messages can betray you through metadata: who talked to whom, when, and how often. Timing patterns and traffic analysis can be almost as valuable to adversaries as the message content itself.
How much do breaches from insecure messaging cost companies?
The financial logic is hard to ignore. The average cost of a data breach jumped 10% in 2023 to $4.88M, according to IBM—driven not just by remediation but by weeks of business disruption and recovery. Shadow data breaches (involving unmanaged or forgotten data stores) cost nearly 16% more, and collaboration platforms are fast becoming prime targets.
Against those numbers, prevention looks cheap. For many CIOs, the math is clear and brutal: spend $50K now to lock down messaging, or spend millions later explaining to shareholders, regulators, and the press why you didn’t.
Which deployment model offers better security: cloud or on-premise?
Secure workspaces aren’t optional—they’re oxygen for modern organizations. Reflecting this urgency, a 2024 CIO survey reported by TechRadar found that 83% of enterprises plan to shift workloads from public cloud to private or on-premises solutions—a trend known as cloud repatriation. This shift reflects organizations' increasing demand for tighter data control, enhanced compliance, and resilience in a complex threat landscape.
| Feature | Cloud | On-Premise |
| Data Control | Limited — hosted offsite | Full — in your infrastructure |
| Compliance | Varies by vendor | Tailored to your jurisdiction |
| Offline Resilience | Internet-dependent | Full functionality offline |
| Custom Security | Limited | Fully customizable |
| Attack Surface | Shared multi-tenant | Isolated, private |
Cloud still shines for speed and scalability. But on-premise wins on sovereignty, resilience, and custom control—especially where regulations demand you know exactly where your data lives.
If I need an on-premises deployment of my team collaboration environment, where do I turn?
If your priority is security and confidence, cloud-first platforms like Slack or Microsoft Teams won’t fit the bill. They cannot be deployed on-premises, which means your data will always reside in third-party infrastructure.
For organizations that require on-prem, options such as BridgeApp or Mattermost provide that flexibility. Running collaboration on your own infrastructure reduces external attack surfaces by keeping every message, file, and policy under your control, meaning they are owned, managed, and encrypted end-to-end. You can decide who has access, enforce password and role policies, and set retention rules aligned with your compliance standards rather than a vendor’s defaults.
This is why on-premises workspaces are often the natural choice for data-sensitive industries where resilience, sovereignty, and regulatory assurance are nonnegotiable.
What should teams demand from secure workspaces?
Security isn’t just a feature set anymore — it’s the foundation of trust. If your collaboration platform can’t deliver on these essentials, it’s not enterprise-ready:
- Role-based access control — least privilege by default.
- Secure file sharing inside chat — so attachments live under the same protections as messages.
- Integrated live-database operations — the ability to work with live data securely (both by humans and AI agents) in the same environment for collaboration.
- Comprehensive audit trails — full visibility into who did what, when, and where.
- Compliance-ready archiving and reporting — built-in support for GDPR, SOC 2, and beyond.
Essential requirement: a secure workspace should feel seamless to users but uncompromising to attackers.
How do teams successfully transition to secure workspaces?
The transition process to a secure workspace doesn’t have to be a marathon. It’s not just about installing BridgeApp on-premise — it’s about bringing your data, your users, and your security practices along with it.
Use Case 1: When Learnify (name changed), a 50-person edtech company, faced a failed SOC 2 audit due to unencrypted message retention within just seven days, they had:
- Deployed BridgeApp on-premise and set up a dedicated VPN for secure access from whitelisted devices.
- Rolled out client apps across employee devices—including preconfigured laptops for new hires.
- Integrated SSO and distributed role-based access, ensuring every user had the right level of visibility.
- Launched AI agents that delivered best-practice security guidance in context, pushed out dynamic nudges to encourage safer habits, and even measured "resilience scores" through lightweight employee surveys.
- Imported existing content and databases from their previous collaboration suite, task tracker, file storage, and CRM.
The results were immediate: zero compliance findings, a 22% faster incident-resolution time, and something harder to measure but just as critical—peace of mind during investor due diligence—knowing that security auditors could review comprehensive logs without finding compliance gaps.
Use Case 2: A Web3 Dev Crew Secures Payments and Compliance
A distributed fintech team building a crypto payment API needed two things above all: airtight compliance and fast incident handling. They rolled out BridgeApp in on-premises mode and immediately put its AI agents to work. Incident Watcher monitored logs in real time, turning errors into tasks and tracking them through resolution. Legal & Compliance Bot continuously checked KYC data and GDPR alignment, eliminating manual audits.
All incident logs, tickets, and compliance documents lived in a single secure workspace, linked directly to tasks and knowledge bases, so developers and compliance officers stayed fully in sync. Most importantly, all client and transaction data remained on their own servers, accessible only through BridgeApp, but fully protected.
The payoff: reaction time to critical events dropped nearly in half, and their latest audit passed cleanly—without extra integrations or weeks of manual prep.
How does BridgeApp deliver both enterprise-grade security and usability across all communication?
BridgeApp unifies encrypted messaging, task management, knowledge repos, and databases with baked-in security. It’s designed to meet the strictest requirements without slowing teams down.
It also provides full control and unified security:
- Complete data control: On-premises deployment keeps all pipelines, data, and messaging in-house. Your infrastructure, your jurisdiction, your rules.
- Integrated Security Model: Access control, and audit logging are applied uniformly across chats, tasks, files, projects, and AI agents.
- Simplified regulatory requirements, from GDPR minimization to SOC 2 audit trails.
- Custom Security Policies: Enterprise licenses include retention rules, granular permissions, and fine-tuned controls to match complex compliance needs.
For CIOs and CISOs, BridgeApp eliminates the old trade-off between speed and security. For everyone else, it just means work keeps flowing with guardrails already in place.
How flexible is BridgeApp when it comes to cloud vs. on-premise deployment?
BridgeApp is built to fit the security posture your organization needs.
- Public Cloud — Run BridgeApp as a managed service if speed of rollout is the priority.
- Private Cloud — Get cloud-like scalability on your own hardware or VPC, with full control over data location.
- Air-Gapped Mode — Physical isolation for defense, R&D, or government environments that demand maximum separation.
Custom Integration — Seamlessly plugs into your existing security stack, from firewalls to SIEM.
What technical safeguards protect data inside BridgeApp?
BridgeApp is designed to protect collaboration at every layer.
- Role-Based Access Controls to enforce least-privilege by default.
- Audit Trails & Compliance Reporting with full visibility into user actions.
- SSO & LDAP Integration for streamlined authentication.
How can teams implement secure collaboration step by step?
A: Rolling out a secure workspace doesn’t need to be overwhelming if you break it into phases:
- Checklist (Day 0): Audit your current tools, map how data flows, and identify compliance gaps.
- 30 Days: Pilot BridgeApp with a core team to validate workflows and security controls.
- 60 Days: Expand usage, migrate legacy history, and enforce retention policies.
- 90 Days: Complete rollout across the company, train staff, and run incident-response drills.
By the end of the first quarter, security isn’t just deployed — it’s embedded into daily collaboration.
What security trends will shape workspaces beyond 2025?
A: The future of secure collaboration isn’t just about stronger walls—it’s about smarter, more adaptive systems. Here’s what’s ahead:
- Private cloud resurgence — fueled by cost-efficiency, sovereignty demands, and scalable control; data-sensitive industries are increasingly migrating workloads back on-premise or to private environments.
- AI-driven deepfake resilience — phishing is exploding in sophistication, requiring workspace platforms to detect and neutralize lies in real time.
- Quantum decryption risk is looming—today’s cryptography could crumble by tomorrow, making post-quantum encryption proof-of-concept deployments a must.
Autonomous workspaces are emerging, powered by AI that self-configures, self-heals, and predicts threats before they strike—bridge the gap between usability and security.
“BridgeApp’s roadmap is built for exactly that future. It includes post-quantum encryption readiness and AI-assisted anomaly detection baked directly into the workspace layer, ensuring that secure collaboration adapts as threats evolve—without ever compromising productivity.
Take control of your data. BridgeApp on-premise gives you complete ownership of your collaboration environment, eliminating third-party risks.
See what BridgeApp — with native AI agents — can unlock for your team.

